3.4.contentACCESS Web Services (Proxy)
Most companies understand that sensitive information/data should be transmitted using a secure connection. TECH-ARROW also reacted on this demand and offers a secure connection, i.e. HTTPS connection to enable communication between the user and the contentACCESS server. To use the HTTPS security, it is required to install a proxy server, which will enable for the user to communicate with the contentACCESS server. The contentACCESS Proxy is one of the contentACCESS components that are included in the contentACCESS setup package.
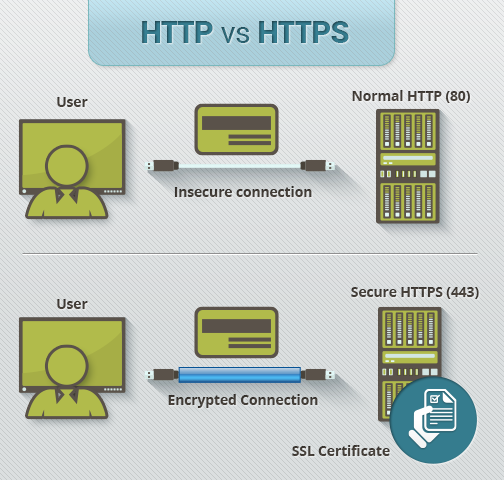
How to allow HTTPS secure connection between the proxy server and the contentACCESS in case of need?
The contentACCESS setup package cannot configure the contentACCESS Proxy to use https on the Internet Information Services (IIS), therefore this must be set manually. It is also necessary to mention that the proxy server must be installed with the “https” connection from the contentACCESS package, otherwise it is not possible to establish HTTPS connection between the proxy server and contentACCESS.
Once the contentACCESS Proxy is installed, continue according to the next steps:
- Open Internet Information Services (IIS) Manager on the computer where the proxy server is installed.
- Import the company’s SSL Certificate
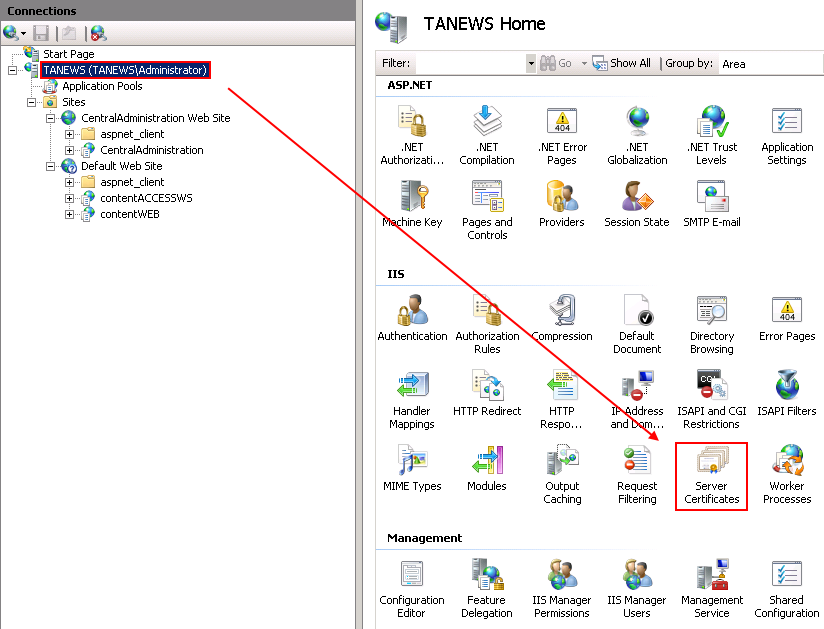
a. Click on the server name – “TANEWS (TANEWS\Administrator)” in our case – and under section IIS double click on Server Certificates:
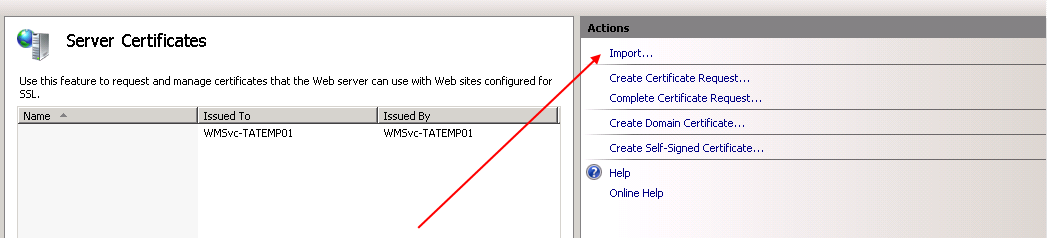
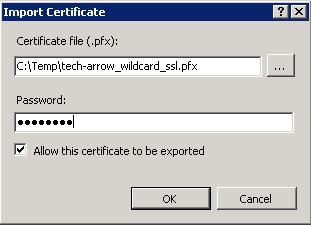
b. Import the certificate. In the upper right corner of the Actions pane click on Import and in the Import certificate window browse for the company’s certificate, open it, then enter the password to it and click on OK:
c. Bindings configuration. Now enable the access to the proxy from HTTPS. Search for the node contentACCESSWS in the Connections pane. Double click on the Default Web Site in the pane, and in the upper right corner of the Actions pane click on Bindings option.

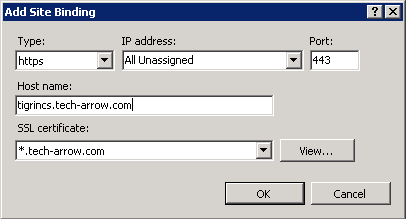
In the Site Bindings window, click on Add. In the Add site binding window, under Type select “https” from the dropdown list, enter the Host name and select the SSL certificate from the dropdown list. Then click on OK.
Cancellation of HTTP-allowance:
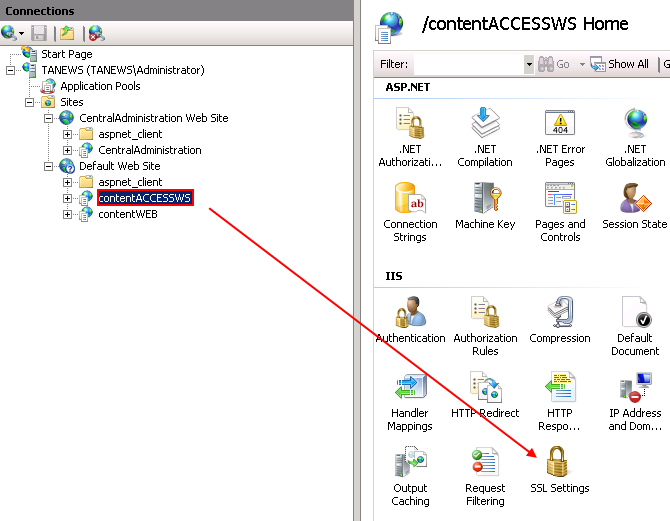
- a) If you would like to stop using the HTTP connection, unfold the appropriate site in the Connections pane and click on the proxy (contentACCESSWS), then double click on SSL Settings option under IIS section (Screenshot A). The SSL Settings page will open. Here check checkbox Require SSL (Screenshot B).
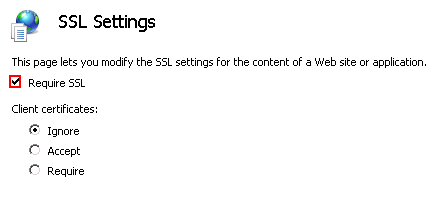
- In the right hand corner click on Apply to save these changes.

To check, if the communication between the proxy and the contentACCESS is well established, enter the following URL into the browser:
https://[HostName]/contentACCESSWS/MobilityService.svc/ping.
If the connection was well established, then the ping result will show OK.
